Cyber-physical systems provide solutions
Network monitoring was created for IT environments, where the chief concern is preventing unauthorized access to information. In such a setting, cutting off intruders’ access to the network and taking devices offline is often a suitable first response to a cyberattack.
OT security, on the other hand, is not as concerned with preventing unauthorized access to information as it is with preventing loss of physical machine and process control. Compromised control comes with varying safety and operational consequences depending on the industry and equipment involved, but maintaining a safe state 24/7 is paramount for all automation and control systems.
For these OT environments where plant and personnel safety are the driving concerns, integrating one or more cyber threat detection tools with PLC logic to act in the event of an attack provides better protection and assurance. This type of cyber-physical incident response solution responds to threat detection by intelligently maintaining uptime of non-infected production cells when possible. It does this by placing infected components into a safe physical state and quarantining them from the rest of the network, and shutting down bad actors’ access into the system.
While many attacks come from outside a local network, an increasing portion originate from within via privileged access. To protect critical production components from both internal and external threats, system architects can place network monitors at individual production cells to trace all traffic to and from the equipment, with PLCs programmed to take appropriate action when attacks are detected (Figure 1).
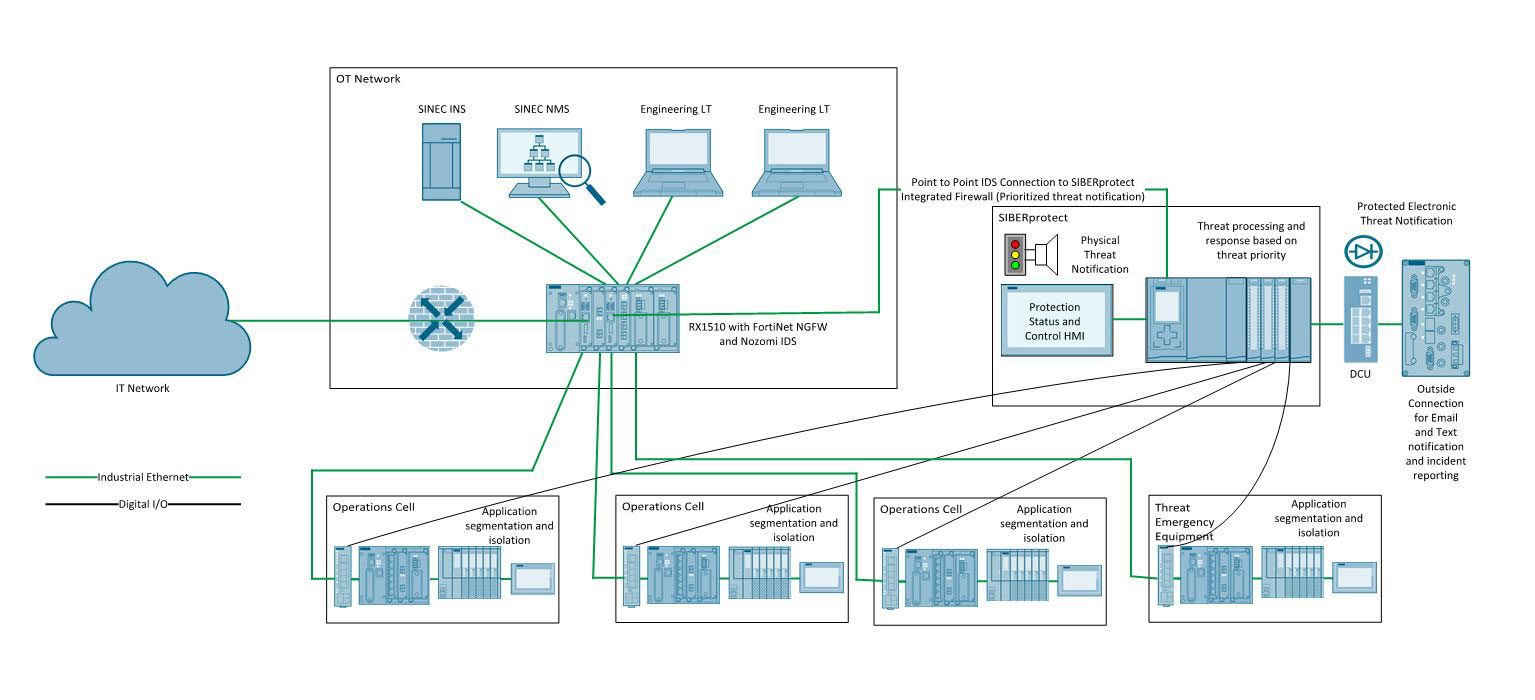
Figure 1: All network traffic between the IT and OT spaces and within production cells is monitored in this example network architecture, with a cyber-physical incident response solution to safeguard equipment.
Upon detection of a threat, cyber-physical protection platforms follow a custom-defined checklist to place production equipment into a pre-determined protected state—not necessarily ‘off’. Non-impacted equipment groups may continue to run, decreasing operational disruption and speeding up recovery time, while infected equipment is quarantined.
These systems are uniquely programmed to fit their specific facilities’ needs of safeguarding from, detecting, responding to, and recovering from cyberattacks. They employ the encryption capabilities found in many modern PLCs, and they can also utilize firewalls, VPN tunnels, digital I/O, and other means of secure communication between intelligent automation controllers and plant equipment. These secure channels provide maximum situational awareness during an attack, while protecting non-compromised devices from infection.
Not all threats are treated equally. Threat detection devices sit to the side, funneling data and analyzing its contents (Figure 2). When a threat is identified, it gets passed to controllers on the network, along with an assigned priority. High-priority threats may trigger network security configuration changes or physical protection responses, while low-priority threats might just alert plant personnel.
